Spam is one of those things on the web that no matter what, you can’t really escape from it. I’ve been posting stuff on the web for years, helped moderate a number of forums etc and always Spam is a problem.
I have this WordPress site you’re reading this post on, and two Drupal sites that I maintain. One of those Drupal sites I do my very best to keep it out of Google, it’s just a personal blog with information only I and maybe my family care about. So it’s got a robots.txt on it and a number of HTTP Headers that are designed to stop it getting any traffic.
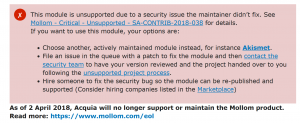
Still it gets Spam. I’ve been writing and posting in that Diary for over 20 years now, so it’s been around a while. For ages I just deleted Spam as it came in, there was only one or two posts a month if even that. Then just as it started to get really bad, along came Mollom. Mollom was a great web service that you just plugged in your Drupal instance and it would flag any new content as either Good, Bad or “Maybe”. Anything Maybe you had to manually review to ensure you weren’t hiding good content. Mollom was an excellent free service, but after many years Acquia decided that it wasn’t a Core Product and terminated it. There’s a great blog post by Dries talking about it and its eventual demise.
Once it died, neither of my Drupal sites were Spam protected anymore and of course the Spam rolled in. I tried a few different things in that timeframe, mostly either “Anti-Bot” type plugins, or Captchas. Captcha seemed like the best solution, but I hated that on this very wordpress blog, whenever I went to login to the Admin panel I would be greeted with a picture where I had to click traffic lights and all that nonsense. And so I moved to hCaptcha and it seemd to be a bit better, but then once again the Spam started rolling in. Not really a surprise when you realise there’s plenty of Captcha Solving Services available. I guess it’s profitable to pay the small fee to be able to post Spam.
Ugh! So again I was back to square one, and even for a time turned off comments on the popular posts on this site that were getting spam. Then I got annoyed and went hunting for a solution and that’s when I discovered Cleantalk.
The first thing I was impressed with is there’s a plugin for both WordPress AND Drupal. With WordPress being the primary blogging platform a lot of people use, I was glad to see Drupal (Which I think is superior myself, but they serve different audiences) hadn’t been forgotten about.
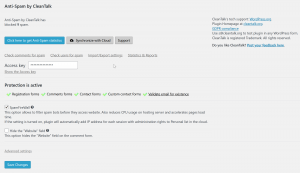
The WordPress Plugin is super easy:
You install it, paste in your key provided by the cleantalk website and off you go. You’re protected from Spam. You can click on “advanced settings” if really need to tweak some settings when you’re using a WordPress Caching plugin, or some of the e-Commerce modules. The Cleantalk WordPress module has settings to make sure all different types of WordPress sites are supported out of the box.
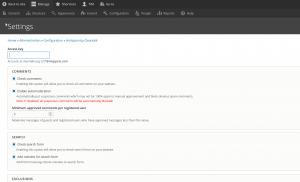
Drupal is a similar story:
Again it’s very easy to setup, you put in your API key and tweak a few settings to how you need them for your setup, and away you go. Your site is protected against Spam!
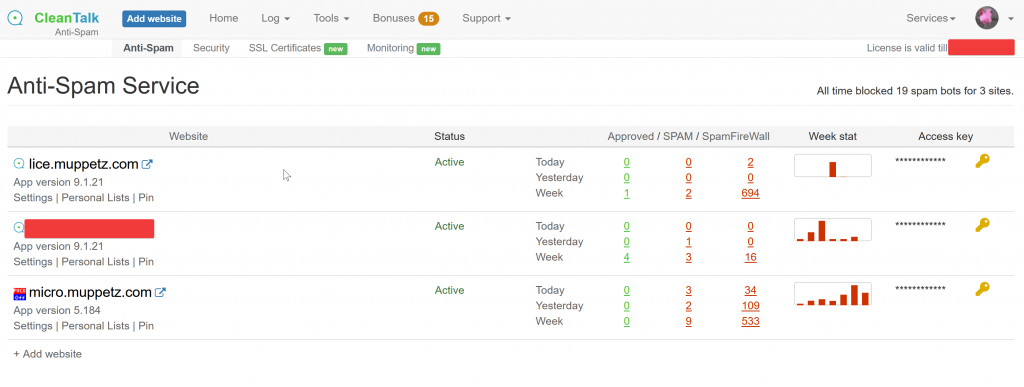
As I said, I’ve got 3 sites. 2 Drupal and 1 WordPress. To see the status of your Spam Protection you just log into the Cleantalk Portal and you get a nice simple overview of your sites:
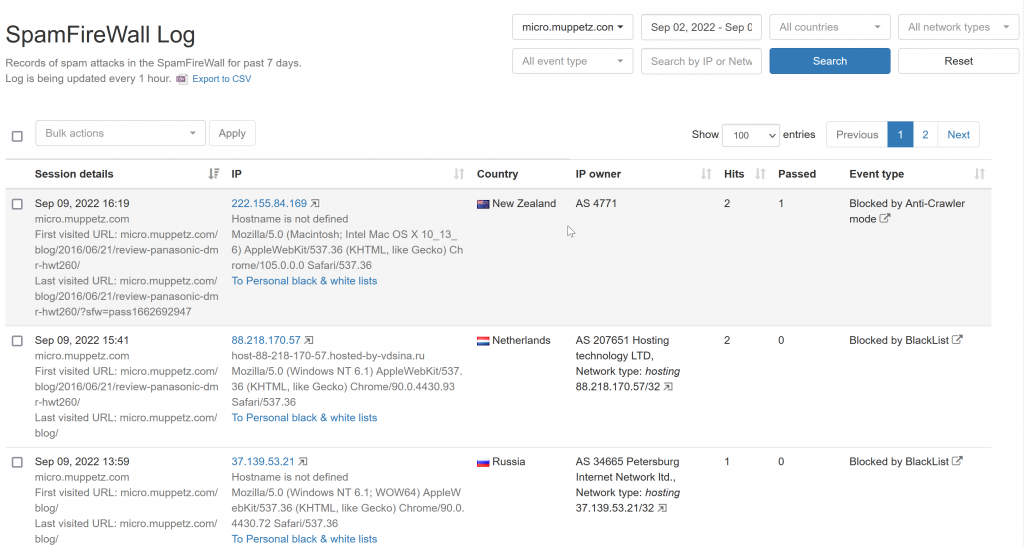
From there you can see how many Spams were blocked before they were even attempted (SpamFirewall), for those spammers lucky enough to get through the SpamFirewall, how many Approved or Spam comments were processed and dealt with.
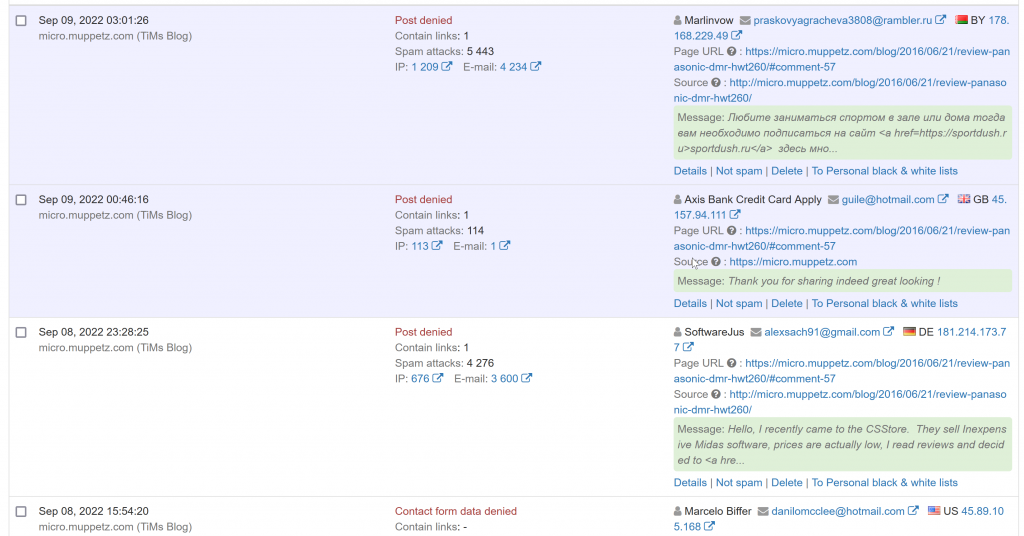
I’ve only been using Cleantalk for a couple of weeks thus far, so I don’t have a lot of Approved comments (my blogs aren’t that popular I guess!) but I sure have a lot of blocked spam. Handbag sales, do I want a video etc. All blocked. No longer do I have to keep comments disabled, no longer do I have to delete comments as soon as they’re posted etc. You can see here the content that Spammers tried to post being denied:
Overall I’m very happy with Cleantalk. It’s fitted in where Mollom left off – automated, hassle free Spam prevention. I think the cost of the service is reasonable, even for a hobbiest like me. I’ve asked a few support questions and both times the support people were very quick to help and offer solutions, and that’s always a good thing.
One final note: I signed up before my trial period (7 days) was over. In doing so, I was granted an extra 6 months free, on top of the 3 years I purchased. In writing this review, I will submit it to Cleantalk and they’ll give me a bonus 12 months of Spam protection. So this post is, in a way, sponsored. But the reason I’d like a bonus 12 months is because I’m very happy with the service they’re providing! So much so I wrote this post.
Thanks for reading. Now go and protect your website from Spam the easy way with Cleantalk!
Tim